November 18, 2014
Watch your cloud environment in a continuous way !
Companies moving aggressively to adopt cloud computing are winning competitive advantage by reducing complexity and increasing business agility, according to a recent study done by the Harvard Business Review Analytic Services.
Scale of cloud deployments is growing; multi-thousand-seat deals are increasingly common not only in the US but also in Europe. IT managers are thinking strategically about cloud service deployments; more-progressive enterprises are thinking through what their IT operations will look like in a world of increasing cloud service leverage.
Key issues
Let’s have a look at the following key questions:
- How many cloud providers does your company deal with ?
- Which strategic activities of the value chain are outsourced into the cloud?
- What are the main cloud assets to protect? How are they protected?
- Who is responsible for their protection? What is the acceptable level of risk ?
- How would the organization react facing a major incident?
- Are we in compliance with the requirements of shareholders and regulators?
- Do we respect the contractual and commercial requirements with our customers?
- Which are the cloud based applications having the highest risk level?
- What is the risk level of all of the cloud based applications?
- What is the risk level of your CRM application?
You can not answer these questions quickly ??!! Just relax, you’re not alone !!!
According to the COSO (Committee of Sponsoring Organizations of the Treadway Commission), the kinds of risks are the same with systems in the cloud as they are with non-cloud technology solutions. An organization’s level of risk and risk profile will in most cases change if cloud solutions are adopted (depending on how and for what purpose the cloud solutions are used). This is due to the increase or decrease in likelihood and impact with respect to the risk events (inherent and residual) associated with the cloud services provider that has been engaged for services.
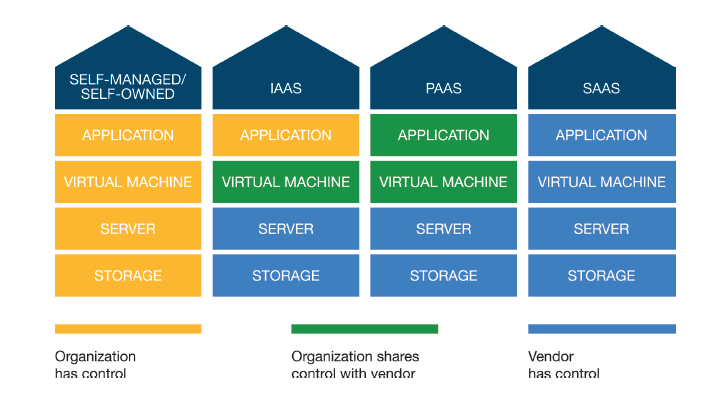
The difference introduced by cloud computing is that some control responsibilities might remain with the organization while certain control responsibilities will be transferred to the CSP as shown below
Establish a strong cloud computing governance
However, the advent of cloud computing should be considered an event in the operating environment of an organization’s ERM (Enterprise Risk Management) program.
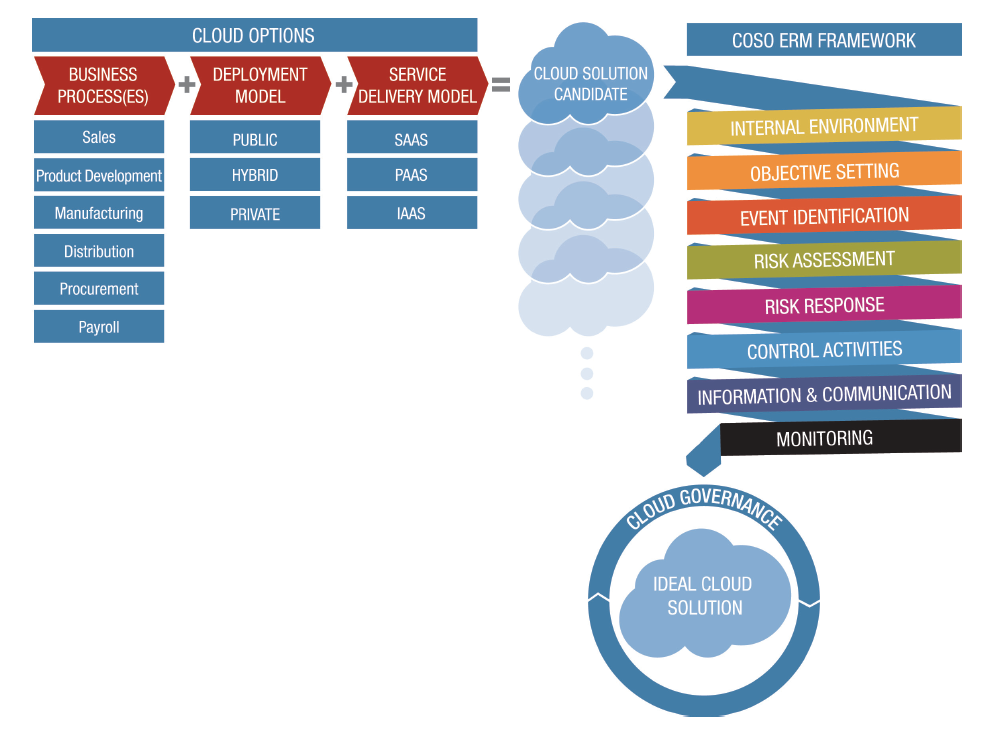
As result, in your journey with the cloud, you shall establish cloud computing governance using the COSO Framework (source Enterprise Risk Management for Cloud Computing), dealing with the following items: internal environment, objective setting, event identification, risk assessment, risk treatment, control activities, information and communication, and monitoring.
Source: COSO – Enterprise Risk Management for Cloud Computing
For instance:
- Management needs to evaluate how cloud computing aligns with the organization’s objectives. Depending on the circumstances, cloud computing might present an opportunity for the organization to enhance its ability to achieve existing objectives, or it might present an opportunity to gain a competitive advantage, which would require new objectives to be defined.
- Management needs also to consider external environmental factors (e.g., regulatory, economic, natural, political, social, and technological), as well as the organization’s internal factors (e.g., culture, personnel, and financial health), as part of the process when identifying and assessing risk events.
- Management should also monitor external information related to its cloud service provider (e.g., financial reports, public disclosures, regulatory filings, industry periodicals, and announcements by fellow cloud tenants), since certain events impacting the cloud provider or fellow cloud tenants might also have an impact on the organization.
Clear roles, responsibilities and accountabilities should be assigned among the following stakeholders:
- Board of Directors
- Chief Executive Officer
- Chief Financial Officer
- Chief Legal Officer
- Chief Information Officer
- Chief Information Security Officer
- Internal Audit